Beginner-Friendly SOC Architecture on AWS — A Learning-Focused Prototype
Beginner-Friendly SOC Architecture on AWS — A Learning-Focused Prototype
Are you a student or security enthusiast looking to understand how a Security Operations Center (SOC) architecture works? This deep dive introduces a learning-focused, cost-conscious SOC prototype built on AWS using open-source tools. It’s designed to help beginners grasp core security concepts, defense-in-depth principles, and incident response workflows.
⚠️ Important Disclaimer: This is a learning prototype, not a production-ready or industry-standard architecture. It’s specifically designed for beginners to understand SOC concepts in a cost-effective way. Do not use this design for production environments without significant security hardening and professional review.
🔍 Learning Goal: This setup helps you understand how different security layers work together, how logs flow through a SOC, and how automated responses can be implemented. Feel free to modify, simplify, or enhance based on your learning objectives and budget.
🌐 Architecture Overview
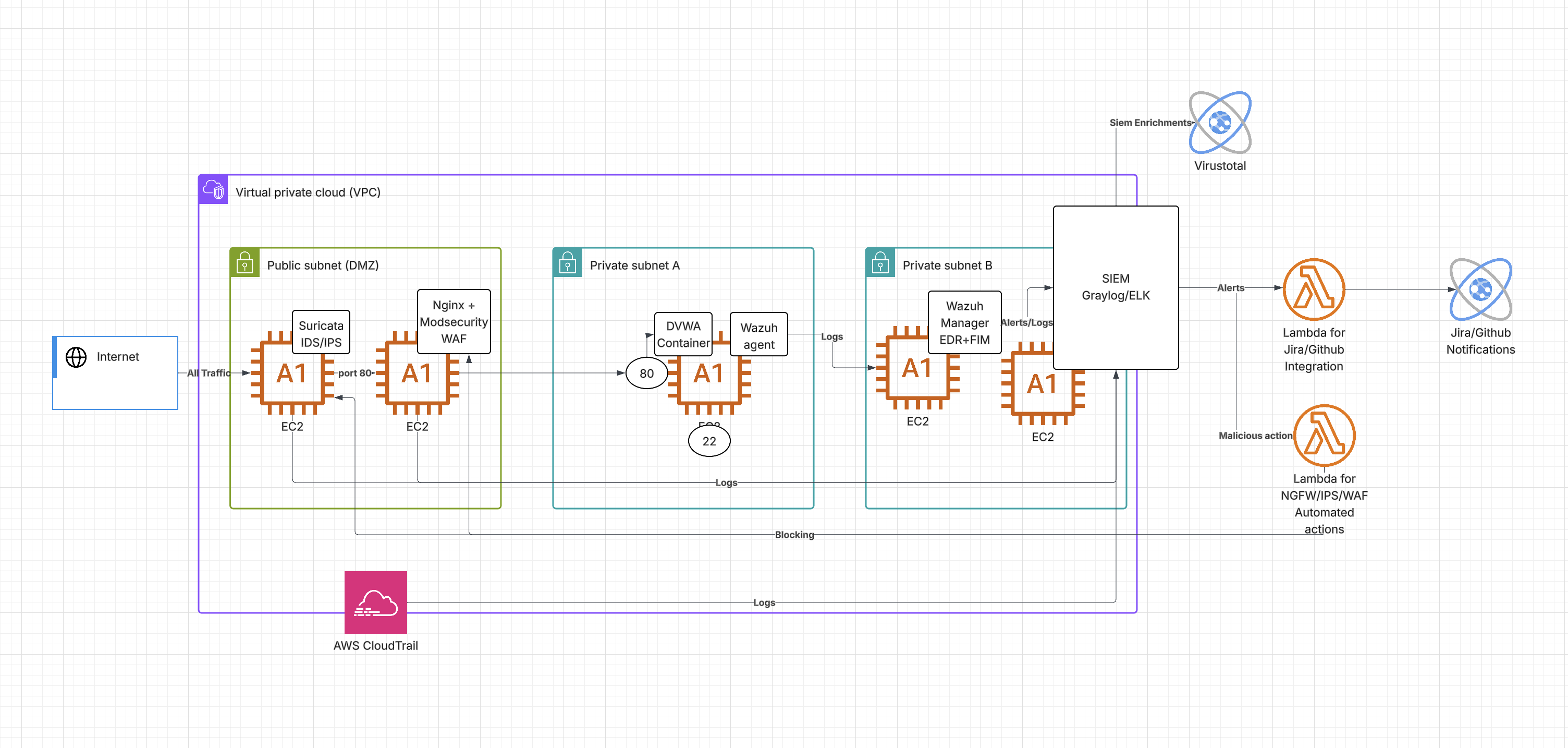 Beginner-Friendly SOC Architecture for Learning Defense-in-Depth Concepts
Beginner-Friendly SOC Architecture for Learning Defense-in-Depth Concepts
This architecture demonstrates defense-in-depth principles with multiple security layers:
- Perimeter Defense: First line of defense against external threats
- Application Security: Web-layer protection and filtering
- Host Monitoring: Endpoint detection and system monitoring
- Centralized Logging: Log aggregation and correlation
- Automated Response: Basic incident response automation
- Cloud Security: AWS-native monitoring and alerting
🏗️ Architecture Components Explained
1. Network Foundation - AWS VPC Setup
VPC (Virtual Private Cloud)
Your VPC acts as your isolated network environment in AWS. Think of it as your own private data center in the cloud where you control all network traffic.
Subnets Strategy
- Public Subnet: Contains internet-facing components that need direct internet access
- Private Subnet: Houses your applications and sensitive systems, protected from direct internet access
Why This Separation Matters
This subnet separation is a fundamental security principle. Your applications don’t need direct internet access - they can receive traffic through controlled entry points (like load balancers or reverse proxies) while remaining protected in private subnets.
2. Perimeter Defense Layer
Option A: pfSense + Suricata (Open Source Approach)
- pfSense: Acts as your network firewall and gateway
- Suricata: Provides intrusion detection and prevention capabilities
- Deployment: Single EC2 instance running both services
- Learning Value: Understand how network-level filtering works
Option B: AWS WAF + Application Load Balancer (Managed Approach)
- AWS WAF: Managed web application firewall service
- ALB: Distributes incoming traffic and provides SSL termination
- Learning Value: Experience with cloud-native security services
Why Two Options? This shows you can achieve similar security goals using either open-source tools (more control, more management) or managed services (less control, less management overhead).
3. Application Layer Protection
NGINX Reverse Proxy + ModSecurity
- Purpose: Acts as an intermediary between external traffic and your application
- ModSecurity: Adds web application firewall capabilities
- Learning Value: Understand how application-layer filtering works
- Placement: In the private subnet, receiving traffic only from your perimeter defense
DVWA (Damn Vulnerable Web Application)
- Purpose: Intentionally vulnerable application for testing your security controls
- Container Deployment: Runs in Docker for easy management and isolation
- Learning Value: Provides realistic attack scenarios to test your SOC
4. Monitoring and Detection
Wazuh Agent (Host-Based Monitoring)
- Deployment: Installed on each EC2 instance you want to monitor
- Function: Monitors system logs, file changes, and suspicious activities
- Learning Value: Understand endpoint detection and response (EDR) concepts
Wazuh Manager + SIEM
- Central Hub: Collects and analyzes logs from all Wazuh agents
- SIEM Capabilities: Correlates events, generates alerts, provides dashboards
- Learning Value: Experience with centralized security monitoring
5. AWS Cloud Security Integration
CloudTrail
- Purpose: Logs all API calls and management actions in your AWS account
- Learning Value: Understand cloud audit logging and account monitoring
- Integration: Feeds logs into your SIEM for correlation with other events
GuardDuty
- Purpose: AWS-native threat detection service
- Function: Analyzes CloudTrail, DNS logs, and VPC flow logs for threats
- Learning Value: Experience with cloud-native security services
6. Automation and Response
AWS Lambda Functions
- Purpose: Automated response to security events
- Examples: Blocking malicious IPs, creating incident tickets, sending notifications
- Learning Value: Understand security orchestration and automated response
External Integrations
- VirusTotal: Threat intelligence for file and IP reputation
- JIRA/GitHub: Incident ticketing and tracking
- SNS: Notification system for alerts
🌐 Optional AWS Networking Components
When You Might Need These (Advanced Learning)
Internet Gateway
- Current Usage: Already included in this architecture
- Purpose: Provides internet access to your public subnet
- Learning Point: Essential for any internet-facing AWS resources
NAT Gateway (Optional Enhancement)
- Use Case: If your private subnet resources need outbound internet access
- Example: Wazuh agents downloading updates, Lambda functions calling external APIs
- Cost Consideration: NAT Gateway has hourly charges - consider NAT Instance for learning
Transit Gateway (Advanced Scenario)
- Use Case: When connecting multiple VPCs or on-premises networks
- Learning Scenario: If you want to simulate a multi-environment SOC
- Example: Separate VPCs for development, staging, and production monitoring
VPC Endpoints (Cost Optimization)
- Use Case: Access AWS services without internet routing
- Example: S3 VPC Endpoint for CloudTrail logs, reducing NAT Gateway costs
- Learning Value: Understand private connectivity to AWS services
📊 How the Architecture Works Together
Traffic Flow (Normal Operations)
- Internet → Internet Gateway → Public Subnet
- Perimeter Defense (pfSense/WAF) → Private Subnet
- NGINX Reverse Proxy → DVWA Application
Security Monitoring Flow
- All Components → Wazuh Agents → Wazuh Manager
- AWS Services → CloudTrail/GuardDuty → SIEM
- SIEM → Correlation & Analysis → Alerts
Incident Response Flow
- Alert Generated → Lambda Function Triggered
- Automated Actions → IP Blocking, Ticket Creation
- Notifications → Email, Slack, JIRA
💡 Learning Opportunities
What You’ll Understand
- Defense-in-Depth: How multiple security layers protect against different attack vectors
- Log Correlation: How events from different sources provide complete attack visibility
- Incident Response: How automated systems can respond to threats in real-time
- Cloud Security: How AWS-native services integrate with third-party tools
Hands-On Skills You’ll Develop
- Network Segmentation: Designing secure network architectures
- Security Tool Integration: Connecting different security tools for comprehensive monitoring
- Alert Tuning: Reducing false positives while maintaining security coverage
- Cost Management: Balancing security capabilities with budget constraints
🎯 Deployment Strategies
Beginner Approach (Minimal Cost)
- Start with just DVWA + Wazuh Cloud (managed Wazuh service)
- Add AWS CloudTrail and GuardDuty (free tier)
- Gradually introduce other components as you learn
Intermediate Approach (Full Learning Stack)
- Deploy the complete architecture in phases
- Focus on understanding each component before adding the next
- Use t3.micro instances to stay within free tier limits
Advanced Learning (Multi-Environment)
- Create separate environments for different scenarios
- Use Transit Gateway to connect multiple VPCs
- Implement cross-account monitoring scenarios
💰 Cost-Conscious Learning
Free Tier Maximization
- EC2: 750 hours/month of t2.micro or t3.micro instances
- CloudTrail: Management events are free
- GuardDuty: 30-day free trial
- Lambda: 1 million free requests per month
- S3: 5GB free storage for logs
Cost Management Tips
- Instance Scheduling: Stop instances when not actively learning
- Log Retention: Set short retention periods for learning environments
- Resource Tagging: Track costs by learning project
- Alerts: Set up billing alerts to avoid unexpected charges
🚨 Important Limitations & Disclaimers
This is NOT Production-Ready
- Security Gaps: Simplified configurations may have vulnerabilities
- Scalability: Not designed for high-traffic or enterprise use
- Compliance: May not meet regulatory requirements
- Monitoring: Limited compared to enterprise SOC capabilities
Learning vs. Production Differences
- Real SOCs have dedicated security teams, 24/7 monitoring, and enterprise-grade tools
- Production Environments require extensive hardening, compliance controls, and redundancy
- Enterprise Architecture includes additional layers like DLP, CASB, and advanced threat hunting
What This Architecture Teaches
- Fundamental Concepts: Core SOC principles and defense-in-depth strategies
- Tool Integration: How different security tools work together
- AWS Security Services: Basic cloud security monitoring
- Automation Basics: Simple incident response automation
🔄 Customization Ideas
Simplify for Budget Constraints
- Remove the SIEM layer and use only Wazuh
- Skip the perimeter defense and focus on application monitoring
- Use AWS WAF instead of managing EC2-based solutions
Enhance for Advanced Learning
- Add VPC Flow Logs for network traffic analysis
- Implement AWS Config for compliance monitoring
- Include AWS Security Hub for centralized findings
- Add Amazon Inspector for vulnerability assessments
Alternative Tool Combinations
- Replace Wazuh with Elastic Security (free tier)
- Use Graylog instead of the ELK stack
- Try Security Onion as an all-in-one security platform
- Experiment with Splunk Free for log analysis
🎓 Learning Path Recommendations
Week 1-2: Foundation
- Deploy basic VPC with public/private subnets
- Set up DVWA application
- Enable CloudTrail and GuardDuty
Week 3-4: Monitoring
- Install and configure Wazuh
- Set up basic alerting
- Practice log analysis
Week 5-6: Automation
- Create simple Lambda functions
- Set up automated notifications
- Practice incident response workflows
Week 7-8: Enhancement
- Add perimeter defense components
- Implement advanced correlation rules
- Practice threat hunting techniques
📚 Learning Resources
Understanding SOC Concepts
- SANS SOC Survey reports for industry insights
- NIST Cybersecurity Framework for structured approach
- MITRE ATT&CK Framework for threat understanding
AWS Security Learning
- AWS Security Fundamentals course
- AWS Well-Architected Security Pillar
- AWS Security Blog for latest practices
Open Source Security Tools
- Wazuh documentation and community forums
- Suricata user guides and rule writing
- ELK Stack tutorials and best practices
🤝 Community and Collaboration
Share Your Learning
- Document your setup process and lessons learned
- Share custom rules and configurations with the community
- Contribute to open-source security projects
Get Help and Support
- Join security-focused Discord servers and forums
- Participate in local security meetups and conferences
- Connect with other learners on social media platforms
🔮 Next Steps in Your Security Journey
Career Development
- Use this experience to understand SOC analyst roles
- Build a portfolio of security projects and documentation
- Consider security certifications like Security+, CySA+, or GCIH
Advanced Learning
- Explore threat hunting methodologies
- Learn about malware analysis and reverse engineering
- Study incident response and digital forensics
Specialization Areas
- Cloud security and DevSecOps practices
- Industrial control systems (ICS/SCADA) security
- Mobile and IoT security monitoring
🧠 Final Thoughts
This architecture is a learning sandbox, not a security standard. It’s designed to help you understand how SOC components work together, how security events flow through different systems, and how automated responses can improve incident handling.
Remember: Real-world SOCs are much more complex, with dedicated teams, enterprise tools, and strict procedures. This prototype gives you a foundation to understand those concepts before moving to production environments.
Start small, learn continuously, and always prioritize understanding over complexity. The goal is to build your security knowledge and practical skills in a cost-effective, hands-on way.
Happy learning and stay curious about cybersecurity! 🛡️
Final Reminder: This setup is purely for educational purposes. Always follow proper security practices and get professional guidance before implementing any security architecture in production environments.